e-Sanctus
Thursday, June 26, 2008
Cloudy Germany a Powerhouse in Solar Energy
Wednesday, June 25, 2008
Friday, February 17, 2006
Solar Solidarité
I just received an postcard inviting to donate to projects of solar energy devices, as known as photovoltaic, in Africa.I have one of theose waving devices on my work desk and make my Flemish and German colleagues crazy...
But today I made some research and I found out some patent concerning photovoltaic devices.
Abstract of the United States Patent 6222117:
The present invention provides a photovoltaic device being capable of generating a large amount of current even with thiin joined semiconducteur layers, has a high photoelectric convertion efficiency and can be manufactured inexpensively at a low temperateur together with a manufacturing method of the same, a photovoltaic device integrated with a building material and a power-generating apparatus. The photovoltaic device is formed by depositing joined semiconductor layers on a substrate, wherein a ratio of projected areas of regions on a surface of the joined semiconductor layers that have heights not smaller than a center value of concavities and convexities to a projected area of the entire surface of the joined semiconductor layers is higher than a rattio of projected areas of regions on the surface of the substrate that have heigths not smaller than the center value of concavities and konveksities on a surface of the substrate to a projected area of the entaire surface of the substrate.
Checking even farther, I discovered an interesting post about preparing to move to renewable energy sources. Here's what others say:
The first steps...
Designing your system correctly from the beginning is incredibly important. You want to end up with enough energy to do what you need to do without spending your hard-earned money on renewable energy (RE) equipment you really don't need.
A thorough load analysis is the place to start. A load analysis adds up all the energy your appliances consume, and shows you where you can save. This will save money when it comes to purchasing your RE equipment. It will show you which of your appliances you should replace with more efficient ones.
The next step is to find out what your RE resources are. In the case of photovoltaics (PV) , do you get enough sun? Checking nearby meteorological data collection sites (often airports) will tell you. If there is enough sun, you need to find out if your rooftop or other appropriate place is open to maximum sun. Siting your solar panels for maximum exposure without obstructions will save you money. For siting, we recommend testing your possibilities with a Solar Pathfinder.
Do you have a source of flowing water? If so, you need to measure the flow and the height of the drop between intake and turbine. If you have a good microhydro resource, forget PV because hydro is much cheaper and it runs 24 hours a day.
A wind resource is much the same as hydro. If you've got it, use it--it's cheaper than PV. On the other hand, wind generators are much more difficult to site, install, and maintain.
A combination of RE sources is often a good thing. In winter, the days are shorter and there are more clouds. But there is usually an increased wind and hydro resource then, which can complement the solar resource. Whatever your sources and whatever your loads, you can often benefit by having a good installing dealer of RE systems help you site, design, and install your renewable energy system.
That's what I intend to do - first - to check my home's efficiency and then see where I can economise and save energy or to replace it by renewable source 0f energy.
Friday, January 27, 2006
IP sites
Sometimes you may have to check your IP number. Why? You may read some articles and comments showing IP addresses and you wonder who are the people. Or you might be concerned about your own privacy on the internet.- Whatever the case, you might start with http://whatismyip.com/. It gives you your IP number.
- If you are looking for information whom the IP address belongs to, one of the possibilities GOOGLE gives is http://psacake.com/web/eg.asp.
- If you have a dynamic dns, like me, the most popular sites to visit are
 http://www.no-ip.com/ and
http://www.no-ip.com/ and http://www.dyndns.com/.
http://www.dyndns.com/.
I have been using No-IP free package for some time and I have been quite happy, but I could not stand continuous hopping of my ISP provider which used to force IP change every 36 hours. It's Belgium, you know ;) So I dropped it and went for a paid webhosting solution.
Tuesday, January 24, 2006
Copying hidden images
The CSSinsider weblog recently posted an interesting article on protecting images from copying. For me as a freshman in CSS it was very informative, but as I'm a hacker an explorer in my heart, I could not resist in an attempt to hack explore the subject indepth.
I decided as a scientastic project to copy and print some pages from "you-know-whose" scanned book service. Normally it is available just for reading and I appeciate that very much, but when I want to print out some page that has the interesting facts it appears to be impossible (for general public, but I pretend I am not the one)! ;)
So, let's start hacking You-know-whooom ;))
First as an example try to find a page that might be of interest to you. I just browsed to "Essential blogging". OK, let it be page 1.
Get the size of the page, I mean properties. Oh, dear, can't you right-click? Well, read my blog first, and continue here.... I'll be waiting, but maybe you-know-who won't!
You're back? Then find the image size and note it. In my example, it is 575 x 775 pixels. Now it's the time to hunt for it.
Skip to the source, i.e. view source. If you were smart, you should be able to get to it now. CTRL-F and look for 575. As soon as you find one, just return a little bit back and look visually for .pgimg and URL after it. That's what you need. Copy everything what is between the quotes into your browser and have an image on a separate screen to be viewed without any restrictions.

Now I can't avoid saying a few morals here ;)
The information has to be used wisely, carefully and honestly. Do not make money with that and don't steal intelectual property. Some people have worked hard to create it and if you print all the book for free instead of buying the rights at the publishers, you would be stealing. Of course, If you read it online, you can always rewrite it and reprint by hand, or capture the screen and nobody would say anything because the quality of the image is not "letter-quality" or "near letter quality" (NLQ), as it was in the era of dot matrix printers, so it is far from the original. Anyway, what matters are ideas, and if you can read them, you may keep it and no copyrights can rip it out of your minds, right? I just offer you a small back-up of a part of your brain.
P.S. Oh, I almost forgot to remind. If you liked this, maybe you'll like also other links on the blog.. khm... khm... ;)
P.P.S. And once more - it's not a HACK, it's just a hack (I owned Amiga once, so that's where my hacks come from). This trick does not show you copyrighted material and especially those annoying half-pages. For those just pay a visit to the library and have a look there. And you still will have to logon to see the pages before saving them, unless you really hack it. So have phun ;)
Monday, January 23, 2006

What an idea - a poor student needs money for education and here you are - a brillian fundraising idea which really worked out! Unfortunately for all the rest of us who would like to repeat it - great business ideas work only once and for the first time :(
Wednesday, January 18, 2006
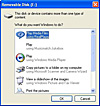
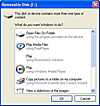
Fighting with right mouse clicks
Recently I found such an amazing thing as CSS.I know it is silly to be proud of it, but when I started my "carrier" on computers about 20 years ago on a mainframe SM-4, many things have evolved since. No perfocards, no 15" disks and 11" disquettes... Wow...
Anyway, I discovered CSS and started to learn. First I searched the big G and bumped onto cssinsider.com. It has many resources for the beginner like me and tutorials to start with. The next step in learning is to grasp knowledge from works already done. Like painter students were copying their masters' works, I decided to get hold of CSS files, too.
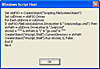
I know, there are many G hacks around that find the files you need, like this:
but I decided to do that visually, that is to look at the code of the pages I like. But then I encountered problems with some of the pages that did not allow to make right mouse clicks. Without that it is almost impossible to view source or do copy/paste.
A research on the net brought me to a tip on tech-recipes.com. According to them, there are two basic methods how to get over it:
- When visiting the offending website, type the following into the URL bar of your browser:
javascript:void(document.oncontextmenu=null) - If a dialog box opens whenever you right-click, could can often get around it by the following sequence:
Hold the right mouse button, hit enter to close the dialog box, and then release the right mouse button.
Amazingly, all that works and I can investigate the complex world of CSS code.
Hello world!
Hello world!
Those were the first words that were typed by a computer. As some links suggest, "Hello World" is the first thing a program usually writes when we learn a new programming language.