e-Sanctus
Thursday, June 26, 2008
Cloudy Germany a Powerhouse in Solar Energy
Wednesday, June 25, 2008
USB hacks
Home > Reference Guides > Security Reference Guide
USB Hacks
Last updated Jul 13, 2007.
How many times have you used a USB stick to transfer files to or from someone else? In this day an age, you are probably guilty of this on numerous occasions. With the ability to just plug your stick in and transfer huge amounts of data, it is just too good of a tool to leave unused. However, the use of these sticks can also be a very risky proposition. In this section we are going to look at some of the ways malicious hackers are abusing this user friendly method of passing data to attack your computers.
Most people think of a USB stick as a passive form of memory. You stick it in your computer, and after a few seconds a popup window appears asking 'What do you want Windows to do?' For all practical purposes, the stick looks and acts like an extra hard drive. While the price is a bit more than a hard drive with the same capacity, the fact that you can keep your files on you at all times is worth any additional cost.
However, a USB stick can be used for more than just a file storage device – you can also run programs from the device. In fact, one software company (U3) has created a business model off this concept and has developed a solution that turns your USB stick into a launch platform for software programs. You can install browsers, Skype, image editing software, document software, and much-much more right onto the stick. Then using a U3 software component that is embedded on the device, you can launch the programs directly from the USB stick without having to install the software on the host PC. While this is a great idea, it also opened up a huge can of worms with regard to autorun capabilities and simplified the process to turn a USB stick into a malicious hackers attack tool.
Building the Autorun Process
There are two main ways to turn a USB stick into an attack tool. The first is to trick the user into executing the payload by convincing them to select the launcher from Windows option menu. This is accomplished by creating an autorun.inf file and placing it on the root of your USB stick. In addition to this file, you need a convincing icon that the victim will click on, and a solid label. When you put all these parts together, you get the following – which is the fake?
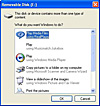
Figure 1: Malicious autorun
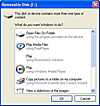
Figure 2: Malicious autorun
As you can see, most people would probably not suspect something was wrong and would readily click on the drive that states "Open Files On Folder". The following is the 'magic' contents of an autorun.inf file on the root of the USB stick that makes this happen. It states the value placed into the Autorun box, lists the icon to be used (you must have this icon on the stick), and specifies the action to be performed when the victim clicks on the icon. Note that this still all requires user interaction.
[autorun] action=Open Files On Folder icon=icons\drive.ico shellexecute=payload.exe
The second method is much more dangerous and powerful. If you recall, U3 has created a software solution that automatically launches its program when the drive is inserted. This is because their software emulates a CD-ROM and USB stick when it is plugged into a computer. Since the Autorun functionality of a CD-ROM is automatic, and requires no user interaction to execute, U3 can ensure that their program will run each time the stick is inserted. Obviously, if U3 can do it, so can an attacker.
In order to setup this type of attack, a person must first obtain a specific type of USB stick. We selected a $20 SanDisk Cruzer with U3 support. Next you have to download or build an ISO containing the autorun files you wish to have executed when the 'CDROM' is created. You can download an ISO from http://www.hak5.org, or build your own with Nero or another type of ISO creating software. We recommend that you download a package from hak5.org and then use the included files to build your own custom solution.
There are two main types of U3 loaders available. The first is the batch script loader that uses the command shell to get the job done. This is pretty much guaranteed to work on any system, but does show a few black boxes very quickly. The second method uses the scripting engine of the operating system, which must be enabled. This method is invisible and as such is the better of the two for covert operations.
If you are going with the batch script option, then in the ISO you will need to place an autorun file that contains the following:
[Autorun] open=start.bat
You will need a start.bat file on the root directory of the stick to make this work. The start.bat file has to contain the code necessary to move the focus of the attack script over to the USB stick. This is only necessary if you need to save files onto the device. Since the emulated CDROM is read-only, any programs that collect information (e.g. passwords) must have the ability to write to the UthSB stick. However, this is where things get a bit tricky because you have no way of knowing what the USB stick's drive letter is. That is why the following code is needed in the start.bat file.
@echo off for %%i in (B C D E F G H I J K L M N O P Q R S T U V W X Y Z) do if exist %%i:\youwillbehackedsoon.txt set dir=%%i cd /d %dir%: cd /d WIP nircmd.exe execmd \WIP\CMD\go.cmd
This script simply scrolls through each letter until it finds a valid drive. Then once it does, it looks for a file named 'youwillbehackedsoon.txt' on the drive to ensure it is the USB stick. Once the file is located, the script jumps to the drive with a CD command and executes the payload (nircmd.exe execmd \WIP\CMD\go.cmd). Nircmd is a program that processes the content of the specified cmd file as a Windows command.
Alternately, you can also use a loader that contains a go.vbe file that is called from the autorun. This go.vbe file is an encrypted 'program' that does pretty much the same as the previous script, except it looks for the file \WIP\cmd\go.cmd, as the following code illustrates.
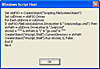
Figure 3: Decrypted go.vbe file.
In this case, the contents of the cmd file are executed by the script shell, which remains invisible.
While most PC's will automatically execute the code, it is best to create your stick with support for U3 autorun and for icon trickery. This way, you can always revert to the more manual option if something goes wrong with the U3 approach.
A modified USB stick can perform many different types of attacks. The actual payload will depend on how the stick will be used. For example, if you are doing a 'drive by' against a PC, you will want the code to be quick, leave behind no indication it ran, and show no popups. In this kind of attack, passwords and information on the PC will probably be the target. However, if you create rouge USB devices and send them to a group of potential victims, then you might want to insert a backdoor with some phone home feature that will allow a remote attacker access to the device, or perhaps just mail out some sensitive information.
USB Payloads
We are going to assume that you will be looking at one of the solutions provide on the Hak5.org site. This means you are going to end up with a stick that scans your computer for sensitive information and saves it to the USB stick.
Thankfully, hak5.org has put together a collection of programs that you can select ala carte at http://wiki.hak5.org/wiki/Switchblade_Packages. The following is a very brief list of the tools that can be included:
System Info: Obtain information some general information about the target system. Dump SAM: Extracts the users/password hashes for off system cracking. Product Key: Extract product keys of installed software programs. IE, Firefox, Messenger Password Grabber: Extract stored passwords of various programs. Windows Update List: Dumps the installed updates. Cachedump: Retrieves the last 10 login caches Port Scan: Lists the open ports on the computer. IE History Viewer: Downloads the full history of the user. Wireless and Dialup Passwords: Retrieves these passwords from the system. Silent VNC Installer: Installs the remote control software VNC and hides it from the user. USB Hack Saw: Installs a program that steals USB stick content. Nmap: Scan targets local subnet for other IP addresses. Folding@Home Installer: Installs Folding client for the hak5 group. NetCat Bindshell: Installs a reverse shell that connects out from the target to a listener. Truecrypt: Decrypts an encrypted version of your tools on the fly.
This list is not comprehensive, and really only reflects a small part of the many malicious programs that could be installed. The limits are up to the attacker's imagination.
Protecting Yourself
Avoiding a USB attack is fairly easy. It only requires a quick registry change that can be done in a few seconds. Just do the following steps (note: messing with the registry can result in big problems for people who do the wrong thing):
Click Start – Run and type in regedit Then go to HKLM\Software\Microsoft\Windows\CurrentVerion\policies. Right click on policies and select New – Key. Type Explorer in the box and hit enter. Next right click on the right side of the open window and select New – DWORD. Enter NoDriveTypeAutoRun and set the value as B5. Close out of the registry editor and reboot.
Once you do this, USB sticks, CDROMs, and DVD's will no longer have automatic autorun power; however, it will still be able to autoplay if you double click on the drive, so be sure to right click on any new drive and select Explore. By tweaking the registry you simply prevent someone from slipping a USB stick into your computer and automatically extracting sensitive data.
You can optionally also just hold down the Shift key when ever you insert a new USB stick that is untrusted. This trick applies to CD's and DVD's as well.
Summary
If nothing else, this section should enlighten you as to the dangers of trusting anyone's USB stick. It should also encourage your to turn off your computers Autorun functionality. USB sticks are a great way to pass around files, both good and bad. For more information on this subject, check out hak5.org's work. Note that not every script up on that site will work correctly out of the box (at least this is our experience). We had to fix some of the batch files that make up the tool kits, but overall the information at this site is excellent!
posted by Sanctus @ 20:09
0 comments
![]()
![]()
...all the hacks and tricks I have done or found or what drew my attention at, admired, learned and finally logged...
Links
Previous Posts
- A washingtonpost.com article from: Elektra@trashym...
- USB hacks
- Solar Solidarité
- IP sites
- Copying hidden images
- The latest news about the million dollar homepage ...
- Fighting with right mouse clicks
- Hello world!
Archives
Please take a look at what proposes Google and help me keep the blog running!


